Every second without protection is an invitation to disaster!
Shield your business against cyber attacks now.
Services
Fed up with patches and half-baked solutions for your digital security?
At CloudSOC Services, we don’t sell smoke.
We offer real security for your data and systems.
Forget about those solutions that promise gold and silver linings but only leave you with more problems.
Here, we play in another league.
Advanced technology for impenetrable security
At CloudSOC Services, we use market-leading tools to secure your business.
Our SOC is mainly based on Azure Sentinel, guaranteeing continuous monitoring and protection.
In addition, for those who prefer on-premises solutions, we offer the implementation of Wazuh, an Open Source SIEM system that we configure and manage on-premises.
Our commitment
Don’t settle for less.
With our solutions, you’ll be protected by cutting-edge technology and a dedicated team of experts.
Trust CloudSOC Services and protect your business against any digital threat.
Target
Defend your Business with a Comprehensive Security Strategy
Did you know that a single cyber attack can cost you thousands of euros and irreparably damage your company’s reputation?
At L4E, our goal is to offer you complete and continuous protection.
With our advanced security solutions, you will have a team of experts monitoring your systems 24/7, detecting threats and responding instantly.
Don’t leave the security of your business to chance, protect yourself with a solid and effective strategy.
SOC and SIEM: Your Shield Against Digital Crime
In today’s digital world, cybercriminals don’t rest.
That’s why you need an impenetrable shield.
Our Security Operations Center (SOC) and Security Information and Event Management System (SIEM) work together to provide you with an unbreakable defense.
We monitor every movement on your network, identifying and neutralizing any suspicious activity instantly.
With L4E, your security is in the hands of the best.
Don’t wait to be a victim, act now and protect your company with us.
Do you have any questions or need help?
If you want to know more or implement our solutions, please contact us.
We are fast, we are safe
Don't Let Hackers Destroy Your Business!
Armor up with L4E's 24/7 Total Protection
Worried that your business will be the next headline of a cyber attack?
With good reason.
In the digital world, cybercriminals don’t rest.
But at L4E, neither do we.
We don’t sell you a couple of firewalls and leave you on your own.
No, my friend. We offer you real protection, 24/7.
Proactive Defense and Immediate Reaction: It’s not just about reacting when you’ve already been hacked.
We analyze every corner of your infrastructure, look for vulnerabilities and eliminate them before the bad guys find them. We protect you with an impenetrable shield.
SOC: The Guardian of your Digital Fortress: A SOC is your private army against cybercriminals. We monitor your systems 24/7, detect any anomaly and respond instantly.
No more sleepless nights worrying about possible attacks.
We take care of it.
Pentesting and Recurrent Audits: We don’t settle for a false sense of security. We do constant pentesting and audits to make sure your system is always bulletproof.
We simulate real attacks to find and correct any weaknesses.
Training and Awareness: Security also depends on people.
We train your team to be prepared for any threat.
Awareness and training courses so that everyone knows how to act in the event of an attack.
At L4E, we don’t just protect your business, we armor it.
We offer you maximum security and peace of mind, so you can focus on what really matters: growing your business without worrying about digital threats.
In today’s world, staying one step ahead is not an option, it’s a necessity.

At L4E, we are not just suppliers, we are partners. Our experience and passion for technology are the guarantee that you will get results, not excuses. If you want your company to stop surviving and start thriving, you know where to find us.
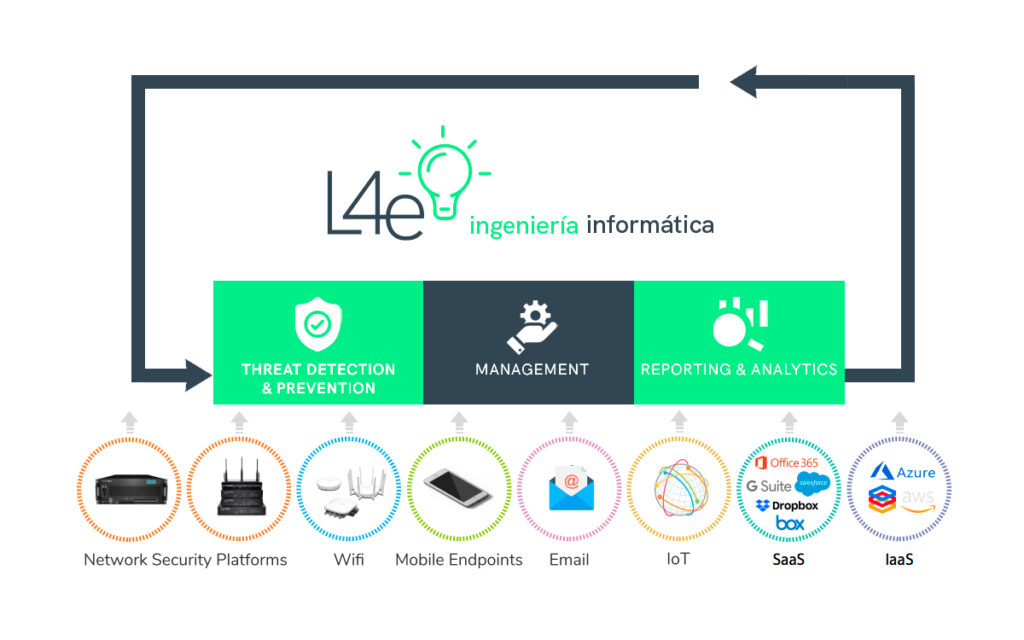
Wake up! Still think your business is safe?
Take a good look at this image.
It’s not just a nice diagram to decorate a presentation.
It is the difference between having your business protected or leaving it open like a house without doors or windows.
At L4E Ingeniería Informática we don’t sell smoke, we sell real security.
Threat detection, efficient management and detailed analysis.
If you are not protecting every point of your network, from security platforms to IoT, you are falling behind.
Sound familiar? It better not
If you think a simple antivirus is going to save you, you’re in the stone age.
Here, every component counts: network security platforms, wifi, mobile endpoints, email, IoT, SaaS, IaaS.
Everything is covered.
There are no excuses.
Our protection is total and covers every possible entry of cybercriminals.
And no, we’re not just another vendor; we’re the ones who will save your bacon when the going gets tough.
Management: No more excuses, only results
Let’s be clear, managing your company’s security is not a game.
With L4E, you have a SOC that works 24/7, without a break, so you can sleep easy.
Do you think we’re exaggerating?
Wait until you get hacked and then we’ll talk.
We don’t sell empty promises here, we sell results.
And if you’re not ready to take security seriously, you’d better go play somewhere else.
Protection
SOC: The Impenetrable Fortress That Protects Your Business 24/7
Security breach
Security breach
Financial loss
Financial loss
Software and system vulnerabilities
Software and system vulnerabilities
Reputational damage
Reputational damage
Data leakage
Data leakage
Regulatory noncompliance
Regulatory noncompliance
Fed up with empty promises and mediocre results? At L4E, we go above and beyond. Our services not only meet, but exceed your highest expectations. We comply with the most rigorous standards, including ISO 27001 and the National Security Scheme, to ensure that your business is protected to the highest level.


No more half-baked solutions; we offer you robust and real security, eliminating vulnerabilities before they become problems. With L4E, your peace of mind is assured. Flirt your business today!
Do you have any questions?
Fill out this form for any inquiry.
That accredits us in our work